The Architecture of Grab's Auth System
We'll talk about PassKeys, their benefits and how they work. Plus, a dive into the internals of Apache Kafka, a compilation of writing advice from the internet's best writers and more.
Hey Everyone!
Today we’ll be talking about
How Grab uses Passkeys for a Passwordless Authentication System
Introduction to PassKeys and their History
How PassKeys work and their Benefits
The Architecture of Grab’s Passkey System
Tech Snippets
Exploring the internals of Apache Kafka
Interview with the Inventors of Deep Research
How My Washing Machine Refreshed My Thinking on Software Effort Estimation
NASA’s 10 Rules for Software Development
A Compilation of Writing Advice from the Internet’s Best Writers
If you’ve ever been caught in a death spiral of shifting deadlines and mounting tech debt, you’re not alone. Developers often face unrealistic timelines that kill team morale and momentum.
Product for Engineers recently published a terrific blog post delving into how they avoid falling into this trap.
Recognize the Vicious Cycle - understand the cause of tight deadlines. Is it over-promising to customers? Poor or unrealistic planning? Work to eliminate the source.
Trust Small Teams - Teams of six or fewer can ship faster than a team twice their size. Small teams means less coordination, fewer meetings and more time coding.
Ditch Arbitrary Deadlines - Focus on real user feedback instead of guesses on timelines from sales/leadership teams.
Hire for Ownership - the best engineers excel when they can drive product decisions. Having a sense of ownership about the product helps drive team morale and momentum.
For more on how to build more effective engineering teams, check out the Product for Engineers newsletter below.
sponsored
How Grab uses Passkeys for a Passwordless Authentication System
Grab is one of the largest tech companies in Southeast Asia. They’re a “super app” and provide services like ride-hailing, food/grocery delivery, mobile payments and more. They operate in over 700 cities and have millions of daily users.
The company offers digital payment solutions (GrabPay Wallet) and lending products (GrabFinance) so secure authentication is a critical component of the app. Phishing attacks, credential stuffing and other common attacks can cost the company hundreds of millions of dollars.
Recently, Grab added support for Passkeys, a passwordless authentication method based on the FIDO standard.
The Grab engineering team wrote a fantastic blog post delving into why they implemented Passkeys, how they work, and the challenges they faced. We’ll be summarizing the blog post and adding some additional context on Passkeys.
Introduction to Passkeys
Passkeys were first proposed in 2009 by engineers at Validity Sensors, a company that developed fingerprint sensors. They were looking for a way to use biometrics for authentication without requiring users to create and remember passwords.
The idea gained traction in 2012 when PayPal joined forces with Validity Sensors to create the Fast IDentity Online (FIDO) Alliance. The goal of the alliance was to develop open standards for passwordless authentication that could be used across different devices and platforms.
In 2018, they released FIDO2, which introduced the WebAuthn standard. With this, users could authenticate with biometrics (Face ID or fingerprint) or a hardware security key instead of a password.
Apple announced broad support for passkeys in iOS 16 (in 2022). Since then, companies like TikTok, Adobe, Amazon, Google and more have added support for passkeys.
How Passkeys Work
Passkeys are based on Public-key cryptography (asymmetric cryptography) where you use a pair of mathematically related keys: a public key and a private key.
The public and private keys are used to create a digital signature that can verify a user’s identity. The private key is kept secret on the user’s device while the public key is stored on the server (can it can be freely distributed).
Passkey Flow
Here’s the steps that happen with passkeys
User Registration - The user creates a passkey for a website with his iPhone. The authenticator on his phone will generate a new, unique public/private key pair using an algorithm like ECDSA. The public key will be sent to the website while the private key will be securely stored in iCloud Keychain
Passkey Authentication - Later, when the user wants to log into the website, he’ll select the “login with Passkey” option. The website will send him a challenge (a random piece of data) to verify his identity. The user will use iCloud Keychain on his iPhone (after authenticating himself with FaceID or touchID) to create a digital signature of the challenge using his private key. This is done with algorithms like DSA or ECDSA
Server Verification - the digitally signed challenge is sent back to the website server. The server uses the public key to verify the signature and grant access to the user.
Benefits of Passkeys over Passwords
Passkeys offer several advantages over traditional passwords:
Convenience and No Password Reuse: With passwords, users often reuse the same password across multiple sites, which creates a security risk if one of those sites is breached. Passkeys eliminate the need to remember passwords, so users don't have to reuse the same password across different services.
Companies don’t store Credentials - explain how Public Key doesn’t need to be kept secret so the company doesn’t have to store anything secret like they do with passwords
Built-In MFA: Passkeys provide multi-factor authentication by combining something the user has (their device) with something the user has (biometrics) or something the user knows (a PIN).
Eliminate Phishing Attacks: Phishing attacks trick users into entering their credentials on a fake website. Passkeys are resistant to phishing because the authentication is tied to the user's device and the specific website or app.
WebAuthn is the web standard that defines the communication between your device, your web browser and the website’s servers. It provides a set of JavaScript APIs that websites can use to interact with a user’s authenticator and specifies the steps for creating/authenticating passkeys.
How Grab Implemented Passkey Authentication
Grab's implementation of passkey authentication follows the standard WebAuthn flow. Here’s the process step-by-step

Creating a Passkey
User Initiates Passkey Creation - The user selects the option to “Enable Passkey” in the Grab app.
Frontend Requests User Data and Challenge: Grab's frontend sends a request to Grab's backend server. This request asks for specific user details and a unique, cryptographically secure random number called a "challenge." The challenge helps prevent replay attacks. The backend will (hopefully) receive the request and reply with the data necessary to initiate the passkey creation.
Frontend Invokes WebAuthn API for Passkey Creation: After receiving the user data and challenge, the frontend will call the WebAuthn API to start the passkey generation process.
Authenticator Creates the Passkey: The authenticator app in the user’s device will receive the request from the WebAuthn API. It will ask the user for consent (with identification through fingerprint scan, facial recognition or a PIN) and then generate a new public-private key pair.
Public Key and Data Sent to Frontend: After creating the key pair, the authenticator will return a PublicKeyCredential object to the frontend. This contains the public key, the credential ID and other relevant data. It does not include the private key. That is kept secret on the user’s device.
Frontend Sends Public Key to Backend: The frontend takes the PublicKeyCredential object and transmits the public key and associated data to Grab's backend server. Grab’s backend will store this info with the user’s account in its database. The public key will be used later to verify the user’s identity when they try to log in.
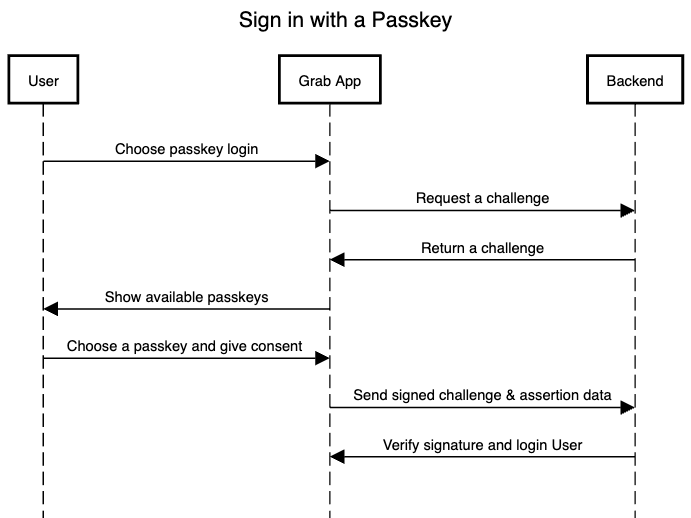
Authenticating with PassKey
User Initiates Sign-In with Passkey: The user opens the Grab app and chooses the "Sign in with Passkey" option.
Frontend Requests a Challenge: The Grab app's frontend sends a request to Grab's backend server, asking for a new, unique challenge. The backend responds with the challenge.
Frontend Invokes WebAuthn API for Authentication: The frontend receives the challenge and calls the WebAuthn API. The Authenticator app (iCloud Keychain for example) will show a list of available passkeys that the user can choose from.
User Selects Passkey and Provides Consent: The user selects the passkey for their Grab account and verifies using facial recognition, fingerprint or a passcode.
Authenticator Signs the Challenge: The authenticator uses the private key associated with the selected passkey to create a digital signature of the challenge and other relevant data. This signature is created using algorithms like ECDSA or RSA. The signed data, along with the credential ID, is packaged into a PublicKeyCredential object.
Frontend Sends Data to Backend - The frontend receives the PublicKeyCredential object from the authenticator. It forwards this to Grab’s backend server.
Backend Verifies Signature and Logs User In: Grab's backend receives the PublicKeyCredential object. It will look up the user’s public key from it’s database and use that to verify the digital signature. If it’s valid (and the challenge matches the one it sent in step 2) then the user can log into their account.
Feature flags are a must for shipping new features quickly and safely. But getting them wrong can be a disaster. In 2012, the high-frequency trading firm Knight Capital famously lost $440 million dollars in just 45 minutes due to a bad flag.
Product for Engineers wrote a fantastic blog post on how to avoid some of the biggest feature flag pitfalls:
Structuring flags safely – Keep them out of your business logic to dodge hidden states and insane debugging sessions.
Killing zombie flags – Old flags can be lethal tech debt, so set up a reliable removal plan.
Ensure graceful failure - Always assume a feature flag can fail or return null. Bugs in the implementation of the feature flag shouldn't break your code.
For more engineering war stories and best practices, check out Product for Engineers. It's free.
sponsored
